Keeping sensitive information secure while enabling business processes
Data security is crucial to any industry that deals with online transactions and communication (for example, through IoT devices). With every exchange of information, the risk associated when transferring sensitive data back and forth becomes multiplied. However, a security solution for this requirement should not hinder any business processes or operations.
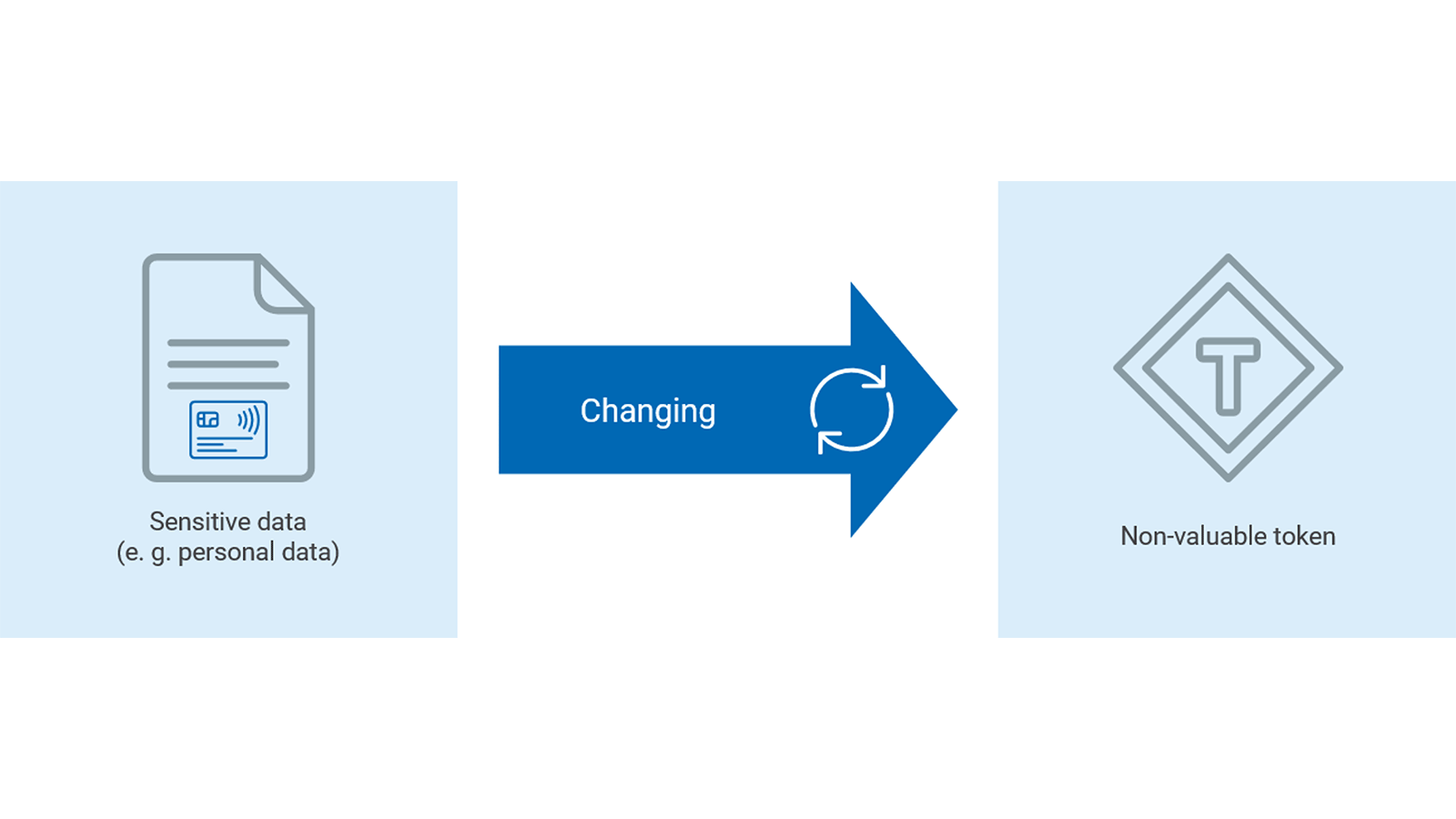
A solution to this problem is tokenization. With a tokenization solution in place, data can be shared without exposing sensitive information. Here’s how tokenization works:
Tokenization turns sensitive data into non-sensitive tokens with the use of cryptographic algorithms. These tokens are an unrecognizable string of characters that are rendered unusable without the tokenization system in place and, if stolen, provide no value to cybercriminals.
What is Tokenization?