Strengthening the cybersecurity and resilience of financial institutions in the EU
In recent years, the EU has pushed forward several initiatives to increase the IT security and resilience of various industries, such as the NIS2 Directive or the Cyber Resilience Act.
As financial institutions are part of the critical infrastructure, the EU Commission has also published a specific framework for this sector, the Digital Operational Resilience Act (short DORA), which aims to ensure the resilience of financial institutions and insurance companies in the event of IT-related operational disruptions.
DORA is a regulatory framework that outlines requirements that financial institutions must follow in order to achieve a common level of security for their network and information systems as well as to their incident response.
Thereby, DORA applies requirements to the following categories:
- Information and communication technology (ICT) risk management;
- Reporting of major ICT-related incidents and notifying, on a voluntary basis, significant cyber threats to the competent authorities;
- Reporting of major operational or security payment-related incidents to the competent authorities by financial entities referred to in Article 2(1), points (a) to (d);
- Digital operational resilience testing;
- Information and intelligence sharing in relation to cyber threats and vulnerabilities;
- Measures for the sound management of ICT third-party risk.
Timeframe of DORA
The Digital Operational Resilience Act (DORA) became effective on January 16, 2023, with a 24-month grace period. Covered entities will be required to comply as of January 17, 2025.
Who is affected?
Article 2 of the regulation defines the following entities that need to comply:
- Credit and payment institutions,
- Account information service providers,
- Electronic money institutions,
- Investment firms,
- Crypto-asset service providers,
- Insurance and reinsurance undertakings,
- Insurance intermediaries, reinsurance intermediaries and ancillary insurance intermediaries,
- ICT third-party service providers,
- And more.
The full list of affected organizations can be found in article 2 – Scope.
The details on ICT-related risks and how to comply
DORA is divided into the following sections:
- Subject matter,
- Scope,
- Definitions,
- Proportionality principle,
- ICT risk management,
- ICT-related incident management, classification, and reporting,
- Digital operational resilience testing,
- Managing of ICT third-party risk,
- Oversight Framework of critical ICT third-party service providers,
- Information-sharing arrangements,
- Competent authorities,
- Delegated acts.
Access the full regulation text here
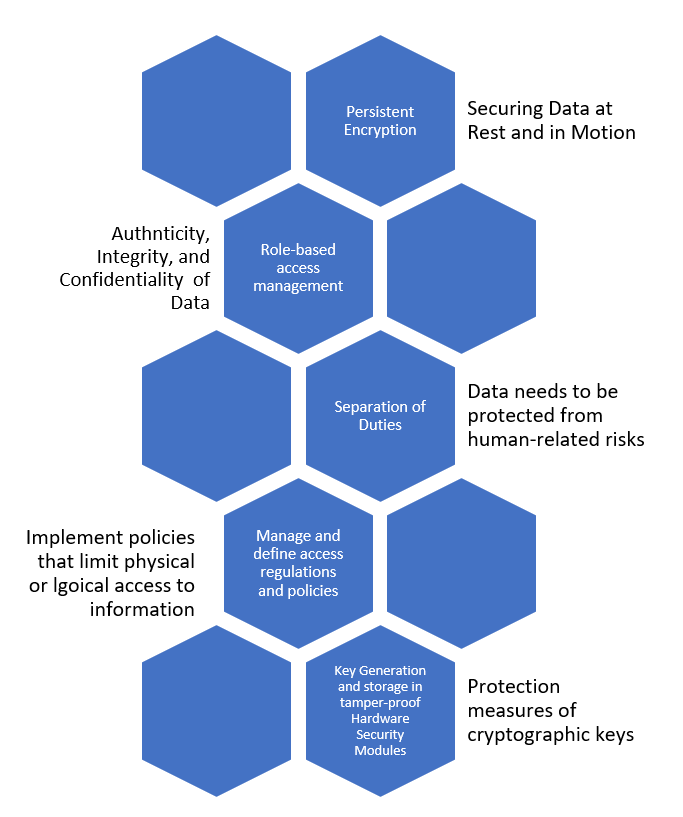
Utimaco’s cybersecurity and compliance solutions help affected organizations comply with DORA’s requirements for ICT risk management as well as ICT-related incident management, classification, and reporting.
Minimize ICT-related risks with reliable file and folder encryption in place.